Only one in three organizations is confident of avoiding a data breach

A majority of organizations are not confident in their ability to avoid major data breaches according to a new study.
The report for breach avoidance company Balbix, based on research from the Ponemon Institute, shows that 68 percent feel their staffing is not adequate for a strong cybersecurity posture and only 15 percent say their patching efforts are highly effective.
Security worries hold back second-hand mobile device market

According to the results of a new study, 58 percent of global consumers have yet to trade in an old mobile device, though 64 percent report they would be willing to do so if more stringent data management processes were in place.
The research by data erasure specialist Blancco shows 66 percent of respondents have some concern that data on their old devices might be accessed or compromised after trade-in.
Could the 3D video selfie replace 2FA?

The industry is constantly looking for ways to bolster login security. Multi-factor authentication and knowledge-based systems are popular but can be cumbersome, so how about using something you carry around all the time, yourself -- or indeed yourselfie?
Identity specialist Jumio is launching Jumio Authentication, a video-selfie authentication tool enabling users to verify themselves during high-risk transactions and unlock everything from online accounts to rental cars, replacing passwords on any device.
Unmanaged open source code could put companies at risk

More than half the code found in commercial software packages is open source, but if it isn’t properly tracked businesses might be in the dark on the number of vulnerabilities and license compliance issues that exist in their applications.
Software supply chain specialist Flexera has released a report looking into the state of open source license compliance, based on analyzing data from 134 software audits.
Phishing gets more personal and harder to detect

An analysis of phishing attacks in the final quarter of 2018 reveals the majority of attacks showed an increase in target personalization, making them considerably more difficult to detect.
The study by email protection start up INKY shows 12 percent of phishing attacks in the period took the form of corporate VIP impersonations, 10 percent were sender forgery and six percent were via corporate email spoofing.
Data integration is the number one challenge for enterprises

Almost half of respondents to a new survey identify ever-increasing disparate data sources as a major pain point.
The study from development technology specialist Progress also finds 44 percent of respondents are worried about integrating cloud data with on-premises data, making real-time hybrid connectivity critical.
Machine learning tool helps prioritize vulnerabilities

One of the keys to keeping systems secure is to effectively prioritize vulnerabilities. Given the volume, with 16,500 new vulnerabilities disclosed in 2018 alone, though this is a tough task.
To help businesses focus on the highest risks, Tenable is launching a new Predictive Prioritization tool that uses machine learning to zoom in on the three percent of vulnerabilities with the greatest likelihood of being exploited in the next 28 days.
New cloud app helps businesses understand their IT environments

As systems become more complex it can be hard for enterprises to understand their IT environment, which presents a problem for operations and security teams.
Cloud-based security specialist Qualys is launching a new IT Asset Inventory cloud application to provide quick analysis of complex and interconnected global IT environments, and help collaboration on security remediation efforts.
Number of DDoS attacks falls but sophistication improves

2018 saw a decline of 13 percent in the overall number of DDoS attacks when compared to the previous year, but cybercriminals are turning to longer, more sophisticated, mixed and HTTP flood attack techniques.
This is revealed in Kaspersky Lab's DDoS Q4 2018 Intelligence Report, which also shows the average attack duration has grown. Compared with the beginning of the year, the average length of attacks has more than doubled -- from 95 minutes in Q1 to 218 minutes in Q4 2018.
Microsoft continues to beat Google in battle of the enterprise apps

A new survey from identity platform Okta shows that 67 percent of knowledge workers prefer Microsoft Word over Google Docs, while only 15 percent report the opposite.
Another 16 percent identify Google Docs as a top-three most frustrating app. When it comes to email, 49 percent prefer Microsoft Outlook over Gmail, while 35 percent report the opposite.
Airline e-ticketing systems put passenger data at risk

Airlines could be putting the personal data of their passengers at risk by using unencrypted links, according to a new report.
Researchers at security and data management company Wandera have uncovered a vulnerability affecting a number of e-ticketing systems that could allow third parties to view, and in some cases even change, a user's flight booking details, or print their boarding passes.
Two-thirds of organizations bypass IT for digital transformation projects

According to a new report released by The Economist Intelligence Unit and sponsored by BMC software, 66 percent of organizations bypass IT when buying new technologies for digital transformation.
But despite this, 43 percent of firms still hold IT accountable if something goes wrong with their digital transformation initiatives.
Google launches new tools to help protect your accounts
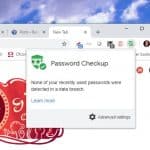
To coincide with Safer Internet Day, search giant Google is launching two new tools to help users detect if their username and password have been compromised.
Google's own research published today shows that many people still reuse passwords. The new tools are designed to raise awareness of account issues.
Most people believe they're more secure online than they really are

New research commissioned by Google, carried out by Harris Poll and released to coincide with Safer Internet Day suggests there is a gap between perception and reality when it comes to online security.
The majority of people (69 percent) give themselves an A or B when it comes to protecting their online accounts -- only five percent give themselves a D or an F. In fact, most people (59 percent) believe that their accounts are safer from online threats than the average person and 61 percent say they are too smart to fall for a phishing scam.
New tool makes it easier to secure IoT devices

Internet of Things devices are appearing in more and more companies, but with them comes the threat of cyberattacks.
To reduce this risk Extreme Networks is launching a simple security solution to help organizations protect unsecured IoT devices.
Ian's Bio
Ian spent almost 20 years working with computers before he discovered that writing about them was easier than fixing them. Since then he's written for a number of computer magazines and is a former editor of PC Utilities. Follow him on Mastodon
© 1998-2026 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.
