PC sales will continue to decline
UK will comply with EU data laws after Brexit

The UK government has confirmed that it plans to comply with existing European laws on data handling and sharing, even after Brexit.
A paper published by the GOV.UK government website said that the EU needs to recognize how the UK is looking for an early agreement in finalizing its plans.
Amazon adds Top Up payment service in UK

Amazon is looking to make it easier than ever for UK shoppers to buy goods on the site using their mobile devices.
The company has this week launched Top Up, a new service that lets users deposit money into their Amazon account simply by scanning a barcode with their phone.
Semi-autonomous truck convoys will hit UK highways by the end of 2018

Small groups of semi-autonomous trucks will be tested on major highways in the UK by the end of 2018.
According to the UK government, Transport Research Laboratory (TRL) has been awarded a contract to test vehicle convoys. These convoys, consisting of up to three trucks, will be traveling in formation, with the leading truck controlling breaking and acceleration.
Acronis Revive 2017 will find and recover lost files

We have quite a few external drives, mostly with content we never use. Backed up old data. It wasn’t that long ago we’d backup data to an external drive long before using the cloud.
You could make use of these drives for other purposes (for example, why not shift your music collection on to one), but you go and wipe the contents and then realize, later, you deleted all your old accounts or important photos. The solution is a file recovery application such as Acronis Revive 2017 -- yes, a brand new consumer tool from Acronis.
Are you doing enough to address your risk? Here are a seasoned CISO’s fundamentals

Several years ago, I received an early-morning phone call at home from one of my security staff. Our security operations center had just contacted us, reporting anomalous data traffic. They believed we had several assets that were infected with malware. As I listened to the incident response team triage the event, I thought to myself, "What can I do as a CISO to better protect my organization?"
I had numerous networks and legacy assets under my purview, and even though I had a solid security program, I didn’t feel we were doing enough to address our risk. What fundamentals could I incorporate to better prepare my teams and my security organization?
Why low-code is key to digital modernization

Low-code application development is increasingly on IT’s radar as application development and delivery (AD&D) leaders and product teams, who are under pressure to support their organizations’ digital modernization initiatives, look for ways to get new applications into production faster. But low-code isn’t just about "time-to-market." It’s about the agility and innovation that a low-code development paradigm can deliver.
Low-code application development platforms provide a drag-and-drop interface to allow programmers -- or even non-programmers with very little training -- to rapidly create applications, saving time during both development and testing. They are mostly offered as cloud native platforms.
FBI wants US businesses to stop using Kaspersky software

The FBI has admitted that it is actively discouraging businesses to not use security products from Kaspersky Lab.
Rob Joyce, the US government's Cyber Security Coordinator, said that the agency has been actively trying to convince companies in the private sector to no longer use products from the Russian security firm following a number of recent concerns.
Microsoft wants you to beta test Windows 10 S

Microsoft has announced a major shake-up in the testing for Windows 10 S.
The software giant has announced that its new OS can now be tried out by all members of the Windows Insiders program.
Multiply the upside of Virtualized Networks with an Integrated Testing strategy

The technology landscape has evolved radically in the last few years and virtualization has been a Godsend to organizations that are looking to drive down their capital and operational expenses while being able to respond to market needs much faster. Interestingly though, while Computing and Storage have progressed leaps and bounds from tapping into the potential of Virtualization, it is only now that Networking seems to be catching on in a major way.
Owing to the massive growth in user traffic due to ubiquitous "digital transformation" occurring across various industries, Global Communications Service Providers are buckling up to improve customer experience by addressing this DEMAND for data with large scale investments in network scalability.
Understanding DevOps metrics

In application, some metric are more suitable to particular processes and organization compared to others. When choosing DevOps for a particular organization, a clear understanding of DevOps metrics tools and cycle is desirable. The role of DevOps is primary for better performance and output regardless of the target organization.
Developments and operations popularly known as DevOps, is enterprise based software that describes the agile relationship between IT operations and development. The primary goal of DevOps is to foster this relationship by promoting better communication between the stated business units.
Estonia wants to launch ESTCoin to complement e-residency program

Estonia is set to emphasize its digital technology prowess with the proposed launch of a new national digital currency.
The Baltic state is considering an initial coin offering (ICO) for the launch of ESTCoin, its very own cryptocurrency,
Google Play apps spread malware through advertising SDK

Through the use of an advertising software development kit contained in 500 apps on the Google Play Store, cybercriminals were able to spy on users and even infect their mobile devices with malware.
That's according to security firm Lookout, which discovered that the Android apps in question all had the lgexin ad SDK built into them which gave unauthorized third parties access to user devices.
How to unlock your Samsung Galaxy Note8

Ladies and gentlemen, it finally happened! Samsung unveiled the Galaxy Note8, one of the most expected smartphones of the year and, most likely, the device that should help the manufacturer fully regain users’ trust, after the entire Galaxy Note7 story.
At first look, it’s an amazing device and, like expected, it also comes with an amazing price. And not in a good way, so we won’t be surprised if a lot of people want to get it with a carrier contract and then unlock it. The good news is that you can easily unlock your Galaxy Note8 now, using a simple and quick method.
Remove stubborn apps, plugins and bundleware using IObit Uninstaller 7
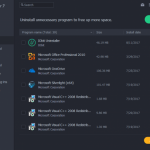
Whilst dealing with malicious software is an ongoing issue, people overlook problematic software, downright stubborn applications and unwanted bundleware that can be difficult to fully remove from your system.
We can’t tell you how many people install security software, uninstall using Add/Remove Programs only to find new security won’t install as the previous suite wasn’t fully removed.
© 1998-2026 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.

