The AI arms race: How machine learning is disrupting financial crime

The financial services industry is in the midst of an unprecedented AI arms race. Criminal organizations are getting smarter, using cutting-edge tech to launch elaborate attacks on financial systems. In response, financial institutions (FIs) are turning to AI and machine learning (ML) to level the playing field. That’s right -- FIs are keeping pace with their criminal counterparts, thwarting malicious activity much more reliably and efficiently.
Having spent my career at the intersection of finance and technology, I've seen the constant race to stay ahead of evolving criminal operations. Rules-based systems, while foundational, simply can't match the speed and adaptability of modern financial crime. But now, through advanced pattern detection, adaptive defense mechanisms, and dramatically improved accuracy in identifying suspicious activity, AI is fundamentally reshaping how we fight financial crime -- and winning.
Gotta go fast! Samsung unveils Sonic the Hedgehog microSD cards

Samsung has partnered with SEGA to introduce a new lineup of Sonic the Hedgehog-themed microSD cards. The Sonic the Hedgehog PRO Plus microSD cards combine Samsung’s storage technology with designs featuring iconic characters, offering fans a functional way to expand their device storage.
The lineup includes designs for Knuckles (128GB), Tails (256GB), Sonic (512GB), and Shadow (1TB), with each card showcasing the character’s face and signature color. Samsung promises “Sonic-speed” performance with read speeds of up to 180 MB/s and write speeds up to 130 MB/s. These cards also feature A2 Application Performance for faster app launches and smoother transitions in gaming.
New investment, state legislation and more penalties -- privacy predictions for 2025
Get 'Resilient Cybersecurity' for FREE and save $39.99!

Building a comprehensive cybersecurity program addresses the current challenges and knowledge gaps in cybersecurity, empowering individuals and organizations to navigate the digital landscape securely and effectively.
With Resilient Cybersecurity readers will gain insights into the current state of the cybersecurity landscape, understanding the evolving threats and the challenges posed today. This book emphasizes the importance of prioritizing well-being within the cybersecurity profession, addressing a concern often overlooked in the industry.
Decentralized solutions, knowing your developer and AI apprentices -- development predictions for 2025

In the past year economic and business pressures, the rise of AI technologies talent shortages and more have put a strain on code pipelines and increased demands on developer teams. This in turn leads to fears around developer strain, product launch timescales and cybersecurity risks.
So what might 2025 have in store for developers? Here's what some industry experts think.
INTERPOL says we should rename pig butchering to romance baiting to avoid victim shaming

There are always lots of financial scams running online, and pig butchering is currently one of the most commonly used techniques for parting victims from their money.
But INTERPOL doesn’t like the term, saying it is shaming and puts people off reporting crime. The international crime-fighting agency believes that a shift to the rather fluffier sounding “romance baiting” is important.
Intel has released one fix for poor Arrow Lake performance, and has another in the pipeline

Intel’s recently released Arrow Lake processors were notable for the wrong reasons. Performance was found to be more than a little disappointing, particularly for gamers. A fix was promised, and one has been delivered.
The fix takes the form of a not only an update to Windows, but also a BIOS update. But it does not end there. Intel says that it will be releasing a further update in January which will introduce additional performance optimizations.
At long last, Microsoft makes it possible to use your webcam with multiple apps simultaneously in Windows 11
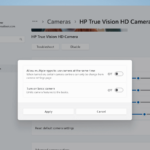
Webcam users rejoice: the end of the “Another App Is Using the Camera Already” error message could be nigh.
People have been asking for the ability to use a single webcam in two or more apps at the same time for what feels likes forever. Built ostensibly as an accessibility feature, Microsoft is finally bringing what it is calling “Multi-app camera” to Windows 11.
StarTech.com launches 140W USB-C GaN wall charger with premium 6-foot cable

StarTech.com has announced its latest product, the 140W USB-C GaN Wall Charger, aimed at providing consistent power for high-performance devices, including Apple’s M4 Pro and Max MacBooks, M3 MacBooks, premium laptops, and other USB-C electronics. This charger is designed to deliver reliable power while minimizing heat during extended use.
The 140W USB-C GaN Wall Charger features a design intended to remain cool even under full load, addressing common issues with overheating in similar products. Product Manager Tony Parackal explains, “This charger is designed to provide an optimal continuous peak power delivery while ensuring user and device safety.”
Threat actors spoof email security providers

A new report from phishing defense company Cofense highlights increasingly sophisticated phishing attacks that are exploiting trusted email security companies such as Proofpoint, Mimecast and Virtru to trick users into disclosing sensitive credentials.
The attacks make use of fake email attachments, phishing links and credential-harvesting tactics to compromise sensitive data. By mimicking well-known brands, threat actors boost the likelihood that the recipients will trust the emails and engage with harmful content, leading to them exposing critical information.
Get 'The Data Science Handbook, 2nd Edition' for FREE and save $60!

Becoming a data scientist is hard. The job focuses on mathematical tools, but also demands fluency with software engineering, understanding of a business situation, and deep understanding of the data itself. This book provides a crash course in data science, combining all the necessary skills into a unified discipline.
The focus of The Data Science Handbook is on practical applications and the ability to solve real problems, rather than theoretical formalisms that are rarely needed in practice.
Credential phishing attacks up over 700 percent

Phishing remains one of the most significant cyber threats impacting organizations worldwide and a new report shows credential theft attacks surged dramatically in the second half of 2024, rising by 703 percent.
The report from SlashNext shows that overall, email-based threats rose by 202 percent over the same period, with individual users receiving at least one advanced phishing link per week capable of bypassing traditional network security controls.
What will attackers target in 2025? CNI, CNI, and more CNI!

Critical national infrastructure (CNI) has had a rough 2024 in the UK when it comes to cybercrime. From the chaos caused by a teenager who hacked into TfL to the dangerous impact on the NHS after the Synnovis breach. And let us not forget the ongoing fallout from the Sellafield breach in December 2023.
These are just a few of the notable cases of a much wider problem, with Bridewell finding that 60 percent of UK CNI organizations experiencing at least one ransomware attack over the past 12 months.
More task focus, the rise of AI whisperers and improved observability -- AI predictions for 2025
Data breach trends -- progress, challenges, and what's next [Q&A]

Despite organizations putting in place better security controls the pace of data breaches shows no signs of slowing down.
We spoke to Jon Fielding, managing director, EMEA at Apricorn, to discuss the latest data breach trends, the progress that's been made and where more work is needed to address security threats.
© 1998-2026 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.